Thanks for the explanation. I’m considering Matrix but will hold off, at least until v1.11 or v1.12 solves the unintended CDN issue described in another comment here, cf https://matrix.org/blog/2024/06/20/matrix-v1.11-release/#continue-reading
- 48 Posts
- 310 Comments
Neat. I wish OpenSSH better support this use case. The instruction involve multiple moving parts on top of OpenSSH (s6-ipcserver, socat or custom scripts) and a number of extra options for the client. That probably adds overhead. It would probably be easier and more efficient if OpenSSH would directly support Unix sockets.
I’m interested into the technical details, not actual URLs. How come servers cited in the video keep hosting/seeding chatrooms despite closing corresponding accounts? Is this impossible due to Matrix’s design, or is it poor moderation from server admins?
About URLs: the author is absolutely right to blur these. The only people he should be sharing this is police, or maybe admins if they’re not aware of the abuse on their server.
That’s the first time I hear of Matrix having this issue.
I’m curious to know more, but the video only cite an anonymous source. Are there evidence or more technical details available regarding this?
Scams, identity thefts, manipulation through targeted ads (eg Cambridge Analytica), malware delivered via ads

 2·8 days ago
2·8 days agoThe incident, he added, amounted to “piracy”.
That exact word came to mind when reading about the incident.
And there is international law on piracy:
there is universal jurisdiction over piracy on the high seas. Pirates are denied protection of the flag state and all states have the right to seize a pirate ship on the high seas and to prosecute in national courts.[

 26·9 days ago
26·9 days agoThey were years ahead of the curve with AI hardware, and they’re well placed to benefit from the AI craze.
Regardless of whether a company’s AI product is useful, or profitable, they need lot of hardware to make it run.

 3·10 days ago
3·10 days agoSoda are incredibly unhealthy, and should be avoided anyway.
In an eye-opening 2024 study of more than 100,000 people, Pacheco found that those who exercised regularly and consumed just two sugary beverages per week had a 15% higher risk of heart disease than active folks who abstained from sugary drinks. Participants who drank two sugary drinks per week and did not exercise were at even greater risk: nearly 50% more likely to develop heart disease.

 3·10 days ago
3·10 days agoFrontex and coast guards in general need oversight. Things can happen out of sight, at sea, there’s a great risk for this kind of behaviour.
Yes, AppImage can run on more distro.
Still AppImage has disadvantages over DEB: No auto-update, No/less system integration, Bigger install packages.
They can’t possibly provide a package for every distro.
Signal’s model, ie keep tight control over development and distribution of the client, and the absence of federation, it well suited for Apple/Google’s stores, but not at all for open-source and Linux’ ecosystem.
Some projects of Signal-compatible clients and forks received a message from a Signal representrive requesting they stop distributing unofficial clients that connect to their servers.
That probably has on shilling effect on Linux distribution that may be considering building and distributing Signal in their repository.

 5·17 days ago
5·17 days agoHe does not look a day over 30

 24·18 days ago
24·18 days agoDon’t waste time trying to reason them. If you’re not able and willing and sue them to enforce the GPL license, the company won’t care.
You should directly informe one of the organisations mentioned previously, they may have a lawyer and experience fighting this kind of fight.
Best you can do youself is collect evidence that they’re distributing modified GPL software, and write a precise description of the issue, to help these organisations kickstart their investigation into the GPL violation.

 4·20 days ago
4·20 days agoNot having the right to work doesn’t necessarily mean asylum seeker won’t work. I suspect it make them more likely to accept undeclared odd jobs. In which case they wouldn’t work less, but would pay no taxes, and have worse working conditions.

 5·22 days ago
5·22 days agoThis is a common issue in software, not limited to scripting. Software are getting more and more layers of wrappers/adapter code, like a Russian doll. It contributes to dependency hell, as each layer brings new dependencies.
Developers often find it easier to wrap existing apps and software, and add another layer on top, rather than improving or replacing what exists.

 23·22 days ago
23·22 days agoNot surprising. If there’s a way for a non-admin user to use this, it means there’s probably a way for a non-admin process to access the data.
Even if if were more secure, there’s probably plenty of ways for attackers to escalate privileges to admin.
The bigger issue is Microsoft providing an official tool for snooping on user activity. Malware won’t have to install their own, and recall taking screenshots periodically won’t be considered anomalous behaviour since it’s an official Microsoft service.

 5·22 days ago
5·22 days agoApparently not yet, astronomers are still waiting for the signal to repeat to appropriately study it.
METI president Douglas Vakoch told Die Welt that any putative SETI signal detections must be replicated for confirmation, and the lack of such replication for the Wow! signal means it has little credibility.[3
For now there are just guesses. If such burst isn’t a fluke and repeats, astronomers will get a chance to better study it and provide a confident explanation.






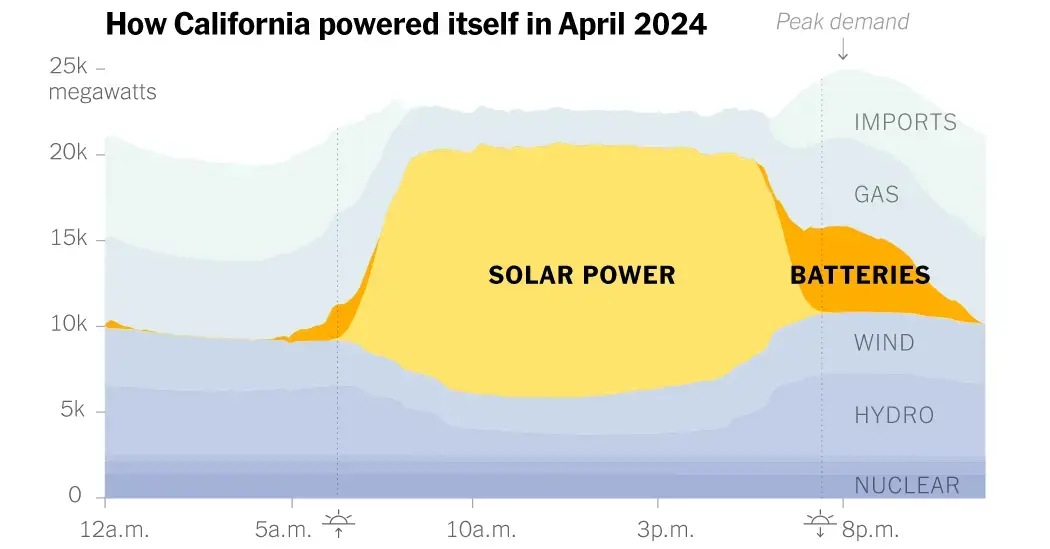

















That sounds a bit contradictory but there’s an important details. Part of the accusation seems to be about picking winners, ie giving subsidies to specific companies rather than the sector as a whole.
If that’s true then a tweak to subsidies might technically solve the issue without solving the EU-China competition balance issue.
IMHO the EU should focus on carbon border tax, and on doing it quickly and efficiently. The idea is taxing import from countries that don’t tax pollution, or at least less than the EU does, to make competing companies subject to similar emissions tax/regulation.